How to Protect Your Computer with Data Execution Protection?

- Source: LaymanZoom
I remember once when my computer was acting slowly, and I discovered that some malicious software was trying to run in the background. Thankfully, my system’s security settings, including Data Execution Protection, blocked it immediately. It felt reassuring to know that this simple feature was working in the background, stopping potential harm without me having to do anything. It is a quiet but effective defense that keeps things safe. Let’s explore Data Execution Protection, understand how it works, and learn how to use it for better computer security.
What Is Data Execution Protection?
Data Execution Protection (DEP) is a safety feature found in most modern computer systems. Its job is to stop programs from running in parts of the computer’s memory that are only meant to store information, not to run code. For example, your computer’s memory is split into different sections. Some parts are for keeping data, while others are for running programs. DEP makes sure that the data is only part of it. Don’t run any unwanted or harmful code on your computer. If something tries to do that, DEP blocks it right away. DEP works in two ways.
One way uses special features built into the computer’s processor means hardware. The other way uses tools in the computer’s software, which means the operating system. These two types of protection work together to keep your system safe from attacks.
How to Use Data Execution Protection (DEP)
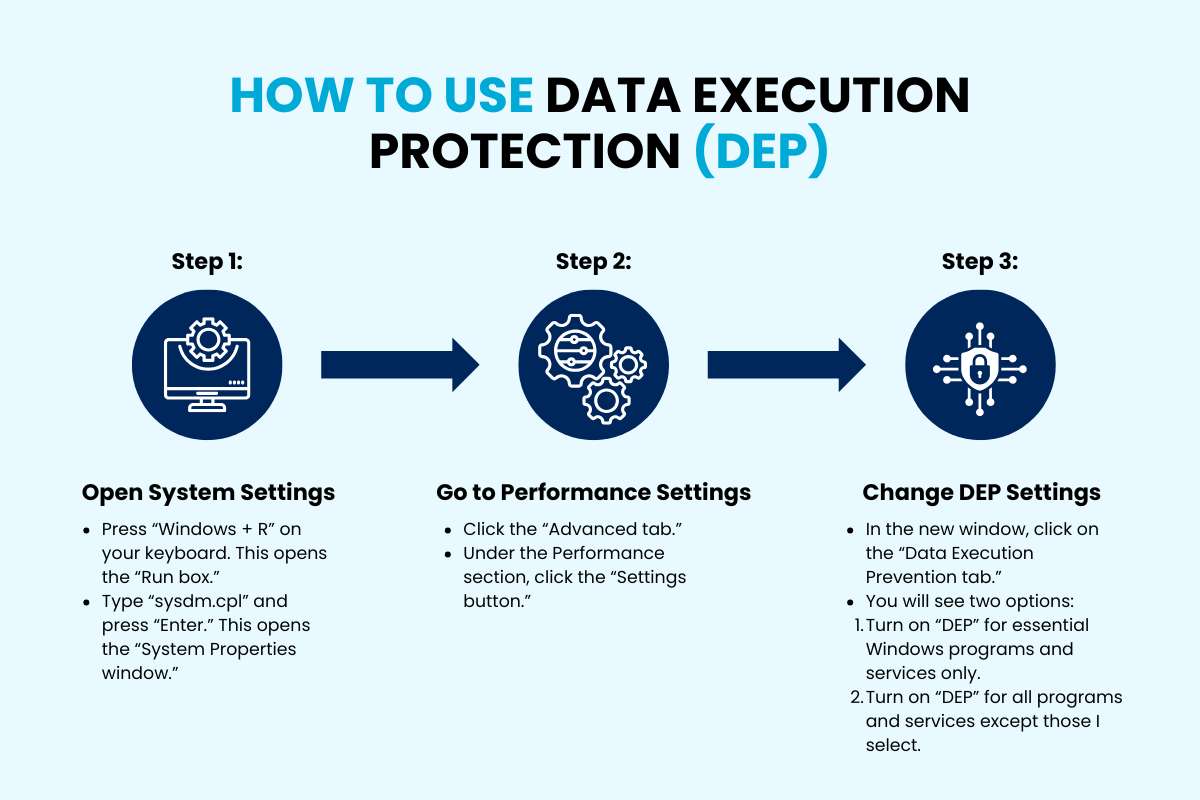
Step 1: Open System Settings
- Press “Windows + R” on your keyboard. This opens the “Run box.”
- Type “sysdm.cpl” and press “Enter.” This opens the “System Properties window.”
Step 2: Go to Performance Settings
- Click the “Advanced tab.”
- Under the Performance section, click the “Settings button.”
Step 3: Change DEP Settings
- In the new window, click on the “Data Execution Prevention tab.”
- You will see two options:
- Turn on “DEP” for essential Windows programs and services only.
- Turn on “DEP” for all programs and services except those I select.
If you choose the second option, you can pick which programs DEP should skip. Removing too many programs from DEP can lower your computer’s protection.
Why Data Execution Protection Is Important?
Hackers may try to take control of a computer by sending harmful code randomly in your memory. Data Execution Protection (DEP) helps stop this by blocking the code from running. Here is why turning on DEP is a good idea,
- Stops common hacks.
- Works with other security tools.
- Makes your system more stable.
Real-Life Example of DEP in Action

DEP and Modern Operating Systems
Microsoft keeps making Data Execution Protection (DEP) better with each new version of Windows. Both Windows 10 and Windows 11 have DEP turned on by default, and it works even better when used with other security tools like Address Space Layout Randomization (ASLR) and Control Flow Guard (CFG). Other systems like Linux and macOS also have similar ways to protect memory. They call them something different, but they all aim to stop programs from running where they should not. To stay protected, users should keep their operating systems up to date. These security tools depend on regular updates.
Tips for Using Data Execution Protection the Right Way

- Always keep it on.
- Always update your system.
- Don’t make too many exceptions.
- Teach your team about DEP.
Conclusion
Data Execution Protection (DEP) is an important but overlooked security feature in modern computers. It helps prevent harmful code from running in memory, blocking many types of attacks before they can do any damage. DEP is simple and built into most systems we already use. If you are using a computer at home or managing a business’s IT systems, keeping DEP enabled can help avoid serious problems. When combined with good security practices, it provides an extra layer of protection. In cybersecurity, every layer matters. While DEP may not be the most noticeable feature, it plays a key role in protecting systems from common threats.
Also Read :- Fortifying Digital Defenses: A Deep Dive into Common Cyber Security Tools